Automated Personal Data Discovery & Linking is the process of discovering personal data stored across all systems and linking it to the individual data owner. PI data linking must be across all systems, including internal systems, third-party systems, SaaS, and IaaS infrastructure. With large amounts of structured and structured data across various systems in an organization, this aspect must be automated. Also, static data flow maps collected from stakeholders are not sufficient and must be supplemented with automated data flow mapping. Enabling full automation to accomplish this link between the PI data and the owner becomes the foundation of many other privacy compliance tasks.
DSR fulfillment is the process of receiving data requests from subjects and taking the necessary steps across all internal and third-party systems used by the organization to comply with the legal right of the data subject. As personal data of the subject is spread across any number of data systems managed by different stakeholders, manual ways to fulfill the subject requests are highly inefficient, costly, prone to error. DSR fulfillment automation is not merely about capturing subject requests and assigning them manually to different stakeholders, based on some static rules. It is the process of full automation of discovery of systems and objects carrying subjects’ personal data, assisting system and object owners by orchestrating DSR fulfillment on these systems, and providing the completed reports back to the issue after taking necessary approvals from the legal stakeholders.
Most privacy regulations prohibit processing personal data unless the organization can establish legitimate interests or the data subject consents to the processing. Regulations also specify that consent is considered valid only if it is freely given, specific, informed, and unambiguous. Consent collection can be explicit (opt-in) or optional (opt-out). In the former, explicit data subject’s consent is needed before the processing of personal data. The latter, personal data, can be processed by providing the data subject the option to object to the processing. If organizations choose to rely on consent for any part of the processing, they must also be prepared to respect that choice and stop that part of the processing if the individual withdraws consent. To establish a lawful basis for processing personal data through consent, organizations must have methods to effectively capture consent at all consent collection points and honor consent revocations for respective data processing activities. Once collected, consent should be linked to unique identities and personal data records within the environment. It should be tracked through its lifecycle so that appropriate remediation steps can be taken when the data subject withdraws consent. Data subjects must be allowed to withdraw consent at any time and without any detriment. Moreover, organizations must maintain updated and comprehensive consent records to demonstrate compliance with the applicable consent requirements.
In case of a data breach or theft of sensitive personal data, almost all the privacy regulations require that all impacted data subjects be notified without undue delay. For example, GDPR breach notification requirements are within 72 hours. To comply with such a short timeline, organizations must have methods to find and link PI data to individuals. Organizations must also have a playbook to automatically form a shortlist of impacted individuals and notify them securely. PrivacyOps automation could help organizations filter incident details, identify the number of impacted data subjects, and automatically discover insights about affected data subjects. With the use of automated People Data Graph technology, organizations can tightly define the pool of data subjects whose personal data has been breached and notify them accordingly.
Privacy regulations require that all internal systems containing PI data go through an assessment process (PIAs, DPIAs, etc.) to understand gaps against the regulations and put controls to fill them and comply with the regulations. These assessments must be updated regularly. Multiple stakeholders typically must be involved in understanding gaps and tracking new controls to be put in place. Assessment automation in PrivacyOps include:
Adopting these practices make the assessment process agile, easier to track, and up to date.
Privacy regulations require that all third parties with whom the personal data is shared go through an assessment process to understand their gaps against the regulation. Performing these assessments with many vendors over spreadsheets and emails is tedious, time-consuming, prone to errors, and hard to track.
PrivacyOps vendor assessment automation uses a system-of-record, a system-of-knowledge, a system-of-engagement, and a system-of-automation to bring all third parties together in one place to communicate privacy needs and complete assessments with one platform.
various third parties on a single, highly-secured platform.
As third parties hold important PD, it’s essential to monitor their independent privacy ratings. These ratings are done based on vendors’ risk assessment, security measures, how they collect, store, and exchange PD with others, respond to data subject requests, and their history of data protection violations.
These independent privacy scores of third-party vendors supplement the responses vendors provide as part of third-party assessment audits. Having a process to monitor any decline in a third party’s independent privacy ratings below a certain threshold enables an organization to swiftly and responsibly deal with privacy issues.
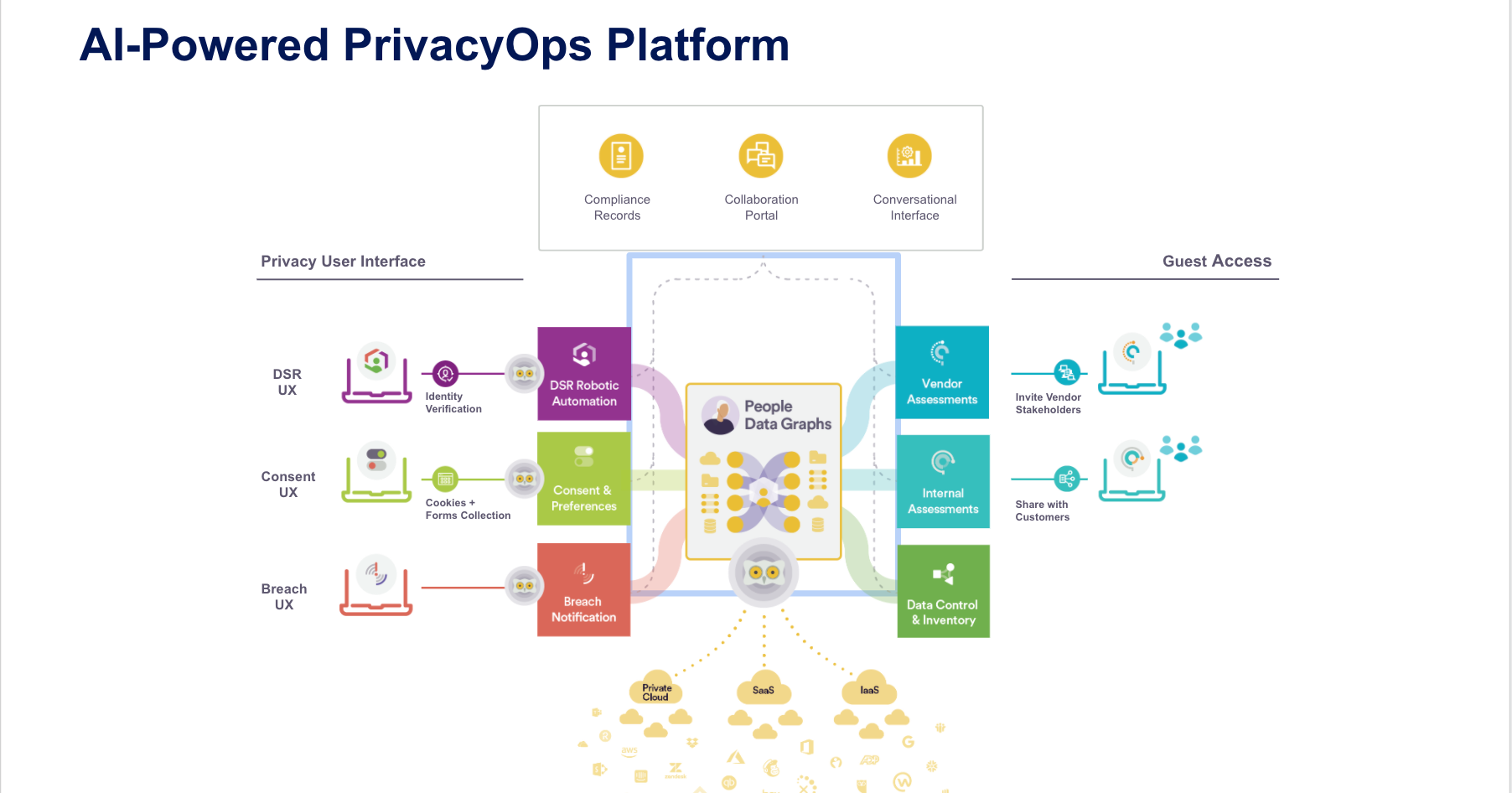
A snapshot of the modern PrivacyOps platform. Each aspect of Data Privacy is addressed by a single platform, ensuring data security and integrity.
[email protected]
Securiti, Inc.
300 Santana Row
Suite 450
San Jose, CA 95128