The PrivacyOps platform envisions the adoption of effective data breach management in two maturity levels: Maturity Level 1 and Maturity Level 2.
The Breach Management Fulfillment Maturity Level.1 helps organizations manage personal data breaches in the following steps:
The PrivacyOps platform enables organizations to build data breach assessment forms to determine the likelihood of impacts and risks an incident may cause to the data subject. It allows anyone who notices or is informed of a security incident to report itvia a self-service portal and incident assessment templates by including the details of the circumstances of the incident, its consequences, the date and time of the occurrence, discovery, and reporting of the incident, as well as the actual cause of the incident, among other relevant details.
| Advantages of Data Breach Intake Assessment and Incident Reporting | |
| Self-service portal | Anyone who notices or is informed of a security incident can submit incidents through an incident logging portal. |
| Incident assessment templates and intake forms | Multiple intake forms are available and configurable to ensure that all relevant details of an incident are captured. |
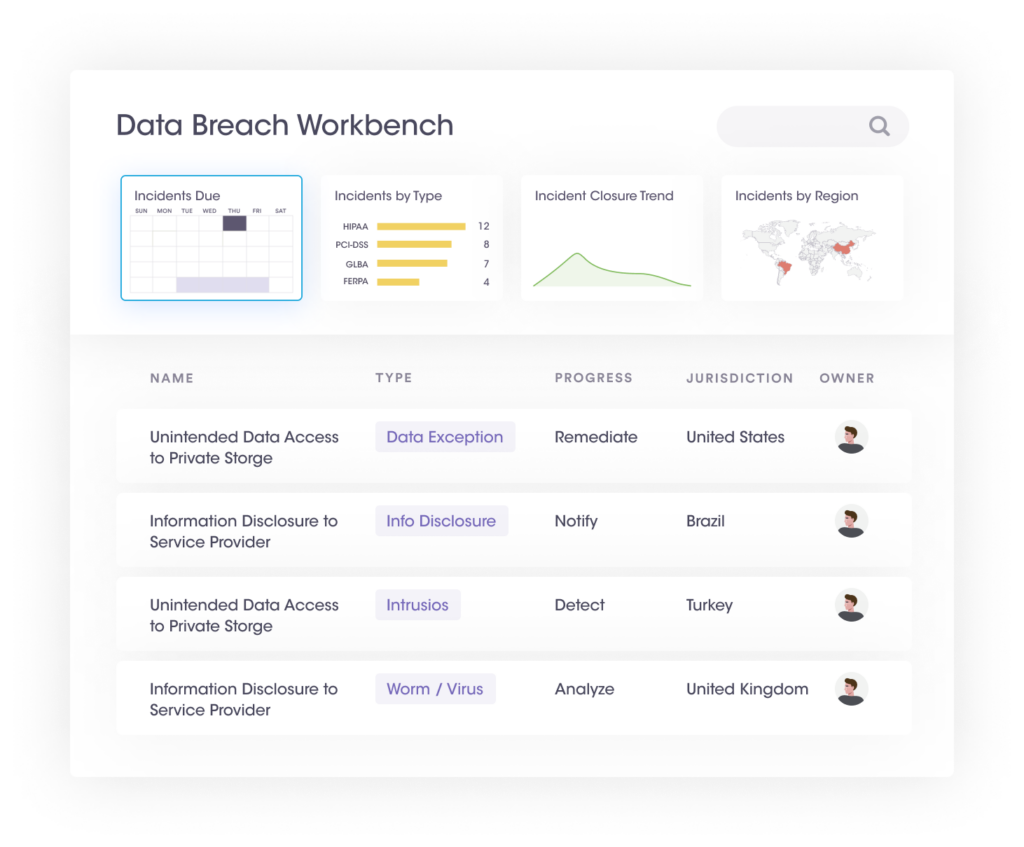
The PrivacyOps platform enables organizations to initiate a data breach management workflow within the data breach workbench when any internal or external security incident is reported. The data breach management workbench gathers incident details using incident assessment templates, assigns responsibilities, and manages regulatory requirements until its closure.
| Data Breach Management Workbench Organization | |
| Incident due date | Shows the current calendar month and indicates all the incidents with their due notification dates |
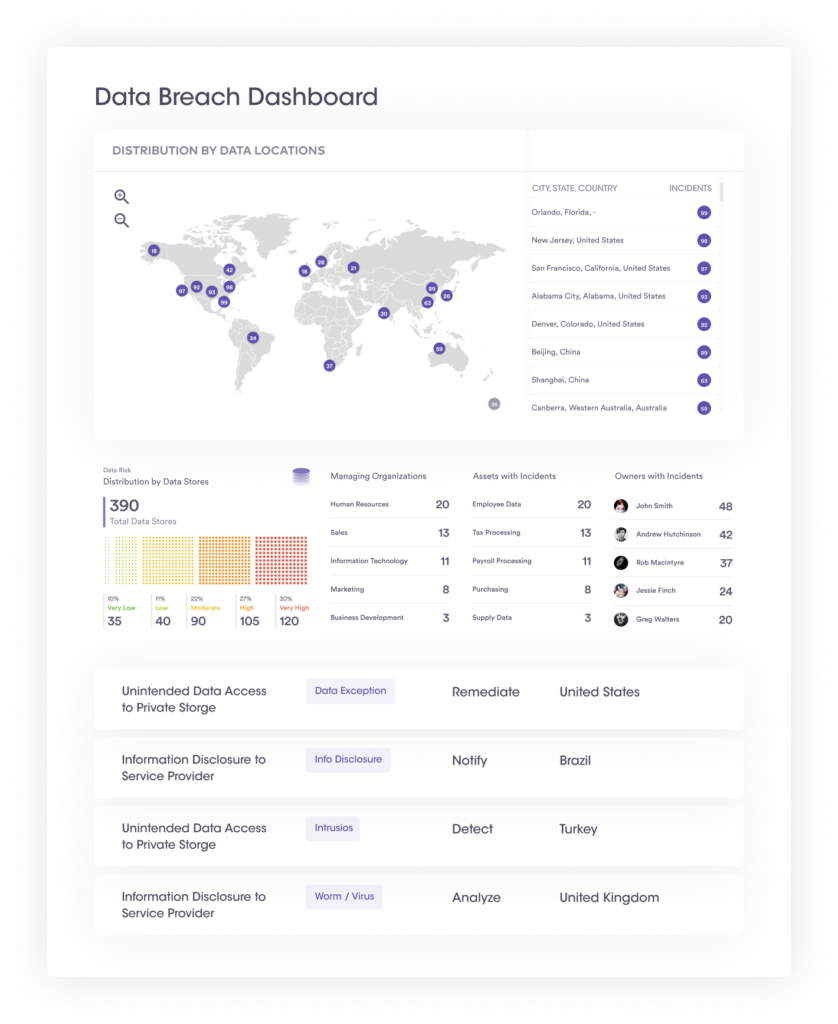
| Incident type widget | Bar chart showing the top 5 categories of incidents. |
| Incident closure trend | Shows two trend lines—the rate of opening vs. rate of closure daily. |
| Incidents by region | The World map shows the regions reporting incidents. |
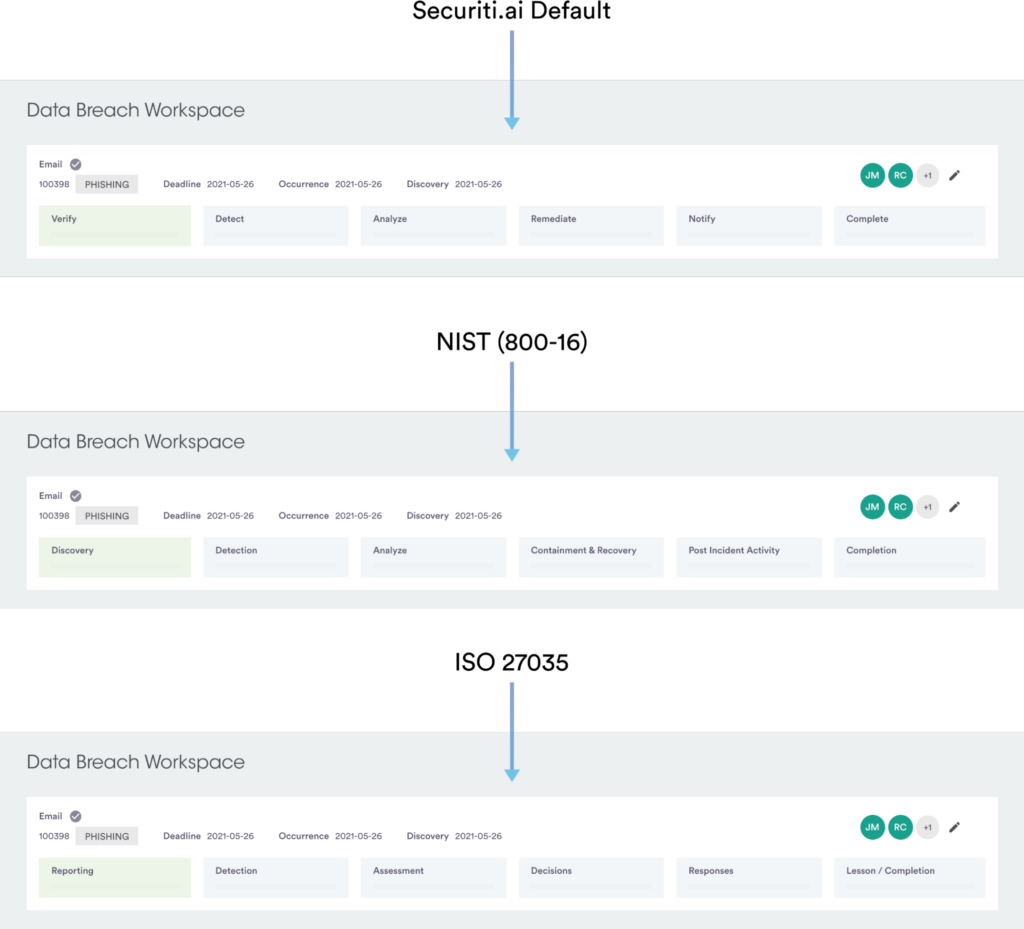
Every incident will go through the incident lifecycle in the data breach management workspace, enabling organizations to identify incident stages and associated tasks. It allows organizations to effectively verify, detect and analyze security incidents and remediate, notify and complete the data breach management lifecycle.
| Data Breach Management Workspace Stages | |
| Stage.1: Verify | Incident owners can review the details submitted by the incident reporter. All the details collected through the assessment or intake form are displayed to the incident owner, who can check the information, adjust details if required and choose to accept or decline. |
| Stage.2: Detect | Organizations may identify and select the appropriate jurisdiction of the incident. This stage allows incident owners to sort through large contact lists and handle independent offline notifications if required. The organization may audit all such actions in the incident audit log. |
| Stage.3: Analyze | The combination of jurisdiction and personal data types involved in the incident could determine the regulations that apply and determine the tasks created in this stage. This stage helps in highlighting penalties for failing to fulfill the breach notification requirements. |
| Stage.4: Remediate | This stage enables organizations to identify the incident’s root cause and capture other remediation details and learnings such as notification methods, deadlines, and notification content. |
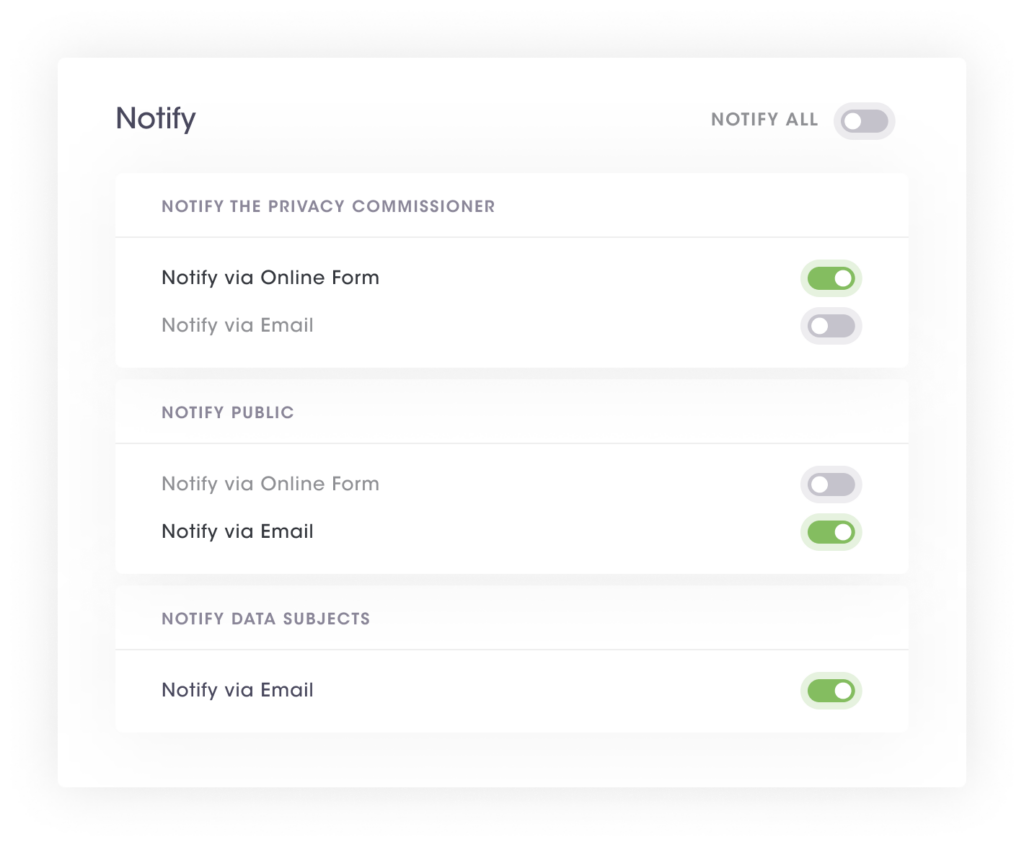
| Stage.5: Notify | This stage allows organizations to notify regulatory authorities by indicating notification time frames, entities to whom notifications are to be made, and possible notification methods for the particular entity. |
| Stage.6: Complete | The completion stage captures the summary of the incident and allows the incident owner to close the incident. Owners can close the incident only if all tasks are approved, and all the notification methods are marked complete in the notification stage. |
Most privacy laws require organizations to document personal data breaches even if it is not required to be notified to the regulatory authority. Such documentation must consist of at least the facts relating to the breach, its effects and the remedial action taken. Dashboards and reports are critical within the data breach management solution, allowing organizations to capture statistics about similar incidents in an incident dashboard and generate a report capturing all incident details.
The Breach Management Fulfillment Maturity Level.2 helps organizations manage the entire breach management lifecycle and fulfill their breach notification obligations through automation.
Organizations that have adopted Maturity level 2 of Breach Management Fulfillment manage the entire breach management lifecycle including all notification obligations through automation. Maturity level 2 has the following four steps:
The first step is scanning data stores and automatically identifying impacted individuals or data subjects. This involves:
(1) filter through all the data to identify and track individuals whose data has been compromised and discover insights about affected data subjects, and
(2) extract contact information from the impacted data or linked data across the organization to optimize the notification process.
With the use of automated People Data Graph technology, organizations can tightly define the pool of data subjects whose personal data has been breached. With the ability to quickly narrow the scope of who is impacted in case of a personal data breach, it becomes possible to limit which data subjects need to be notified, and deliver those notifications within strict reporting deadlines.
Once auto-detection of impacted data subjects has taken place, the PrivacyOps automation allows organizations to narrow down the incident’s scope further so that the incident response can be determined, depending on the jurisdiction where the incident has taken place. For example, a data breach incident of Protected Health Information of US residents would trigger a HIPPA violation and associated notification and remediation activities.
Once the incident response has been determined, the PrivacyOps automation allows organizations to make timely notifications using pre-built templates and prescribed notification formats. Notification requirements vary depending on the type of compromised personal data and the applicable data protection law. For example, the notification methods, entities to notify, notification timeframes, and notification formats may vary for each jurisdiction. However, the PrivacyOps platform uses jurisdictional research data to display correct notification templates and guidelines corresponding to the particular jurisdiction.
The PrivacyOps platform helps organizations to maintain centralized audit trails of how the incident was managed and remediated and other incidents related documentation. Since dashboards and reports are critical within the data breach management solution, Maturity Level.2 allows organizations to capture statistics about similar incidents in an incident dashboard and generate a data breach executive report capturing all details associated with a particular incident. This ultimately enables organizations to demonstrate compliance with the applicable legal requirements.
| Summary of Breach Management Automation | |
| Maturity Level 1 | Maturity Level 2 |
A preformatted intake form with configurable reference lists for easy reporting of breach incidents; An Incident Management Workspace to provide an overview and help manage various breach incidents and connected responses; Verification of incidents by data owners and the selection of affected data stores;Manual input of impacted jurisdictions, personal data types, data subjects, and other important details; Extraction of appropriate regulatory information from a comprehensive database to advise on legal requirements for response or notifications, possible penalties, and further actions required; Analysis of the jurisdictional risk; Creation of tasks (required notifications and methods) leveraging research knowledge along with links for online reporting of breach incident as well ability to create custom tasks ; Checklist for notifications to selected entities (manually); Automated creation of audit log and exportable completion report (CSV format) for data audits | Scan of the affected data stores pre-populates the incident intake form and reference lists for reporting of the breach incident; Auto-selection of impacted jurisdictions, PD types, data subjects, and other details based on data scan result of affected data stores; Automated creation of tasks and notifications to required entities and data subjects through a secure portal for easy management; Notification content auto-populated using results of data scan of affected data stores and regulatory knowledge which can be edited and configured as per user; |
[email protected]
Securiti, Inc.
3155 Olsen Drive
Suite 325
San Jose, CA 95117